Data Leak Prevention
A Unique Context-Based Network Data Leak Prevention
The Data Leak Prevention Solution is an integral part of the Data Security Firewall and acts as a core solution that helps prevent data leak through various platforms. The Data Leak Prevention Solution integrated within the Data Security Firewall identifies, monitors, logs and prevents misuse and exploitation of the data when transferred from your organizational network through deep content inspection and a contextual security analysis of transactions, DLP systems act as enforcers of data security policies. They provide a centralized management framework designed to detect and prevent the unauthorized use and transmission of your confidential information. DLP protects against mistakes that lead to data leaks and intentional misuse by insiders, as well as external attacks on your information infrastructure.
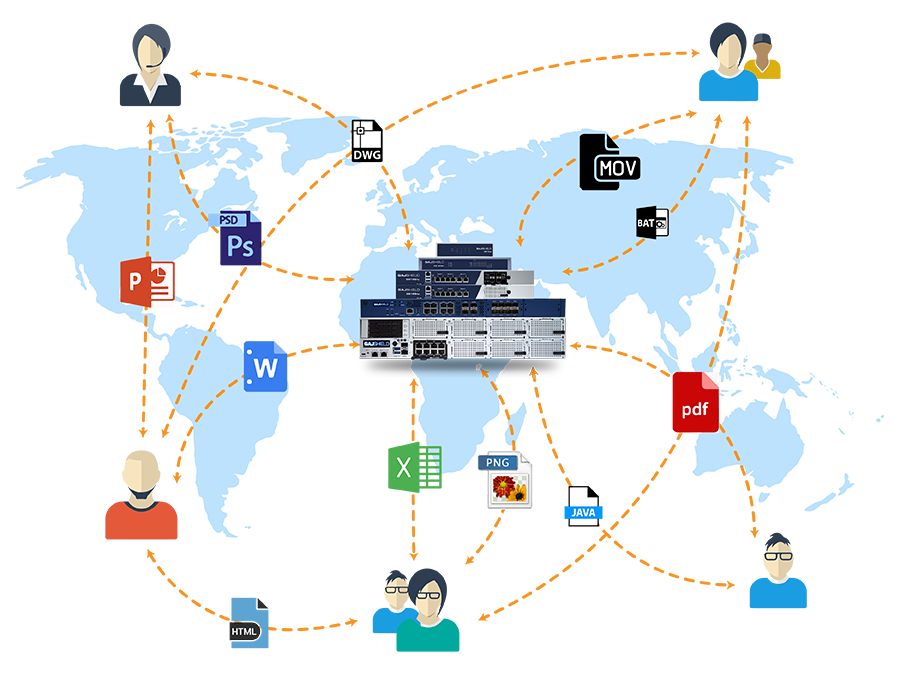
Features of GajShield Gateway DLP:
- Protect Business-Critical Data.
- Protects Data in Motion.
- Protect from Intentional and unintentional Data Leak.
- Prevent IT Shadow
- Agentless solution
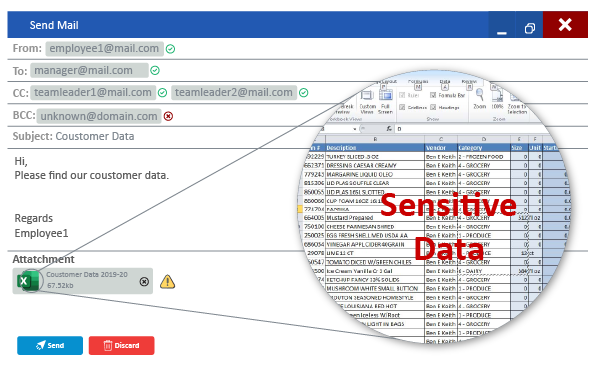
Prevent Sensitive Data Leak
Advantages:
- Deep inspection of application data:
Deep dive a layer into applications by using deep inspection and contextual intelligence engine to create data context, beyond just the application contexts. For better, deeper information visibility and better security. It can prevent data leak based on contextual parameter on both application and data level like restricting ‘From’, ‘To’, ‘Subject’, ‘Email Data’, ‘Attachments’ etc. in email applications and other parameters for various other SaaS Applications.
- Control Data inflow and outflow:
Gain complete control over what goes and comes into your network. Now set policies to allow or block certain content to be sent out or downloaded of the network to control the inflow and outflow of the data.
- Context-sensitive data leak prevention
Using contextual intelligence, now you can define data leak prevention policies based on textual content inside the file. The DLP can block file based on textual content it carries. For example, If in an organization, keywords like “tenders”, “Quotation” are blocked, the users will be restricted to send emails or documents and attachments consisting of these keywords words. The Deep Packet Inspection inspects the file content attached to a mail, being uploaded to a file-sharing application, file sharing application, social media etc.
- Block Allow Data type, file extension, file content and more.
Explore the possibilities of blocking and allowing file type that can be downloaded or uploaded using the Data Leak Prevention solution that has the capability to identify the file type and its extension.
- Prevent Data Leak on SaaS Applications.
GajShield’s CASB (Cloud Access Security Broker) works on a proactive detection model to ensures that all the communication between the on-premise device and cloud application provider complies with the organization’s security policies. It uses information from the Contextual Intelligence Engine, check for compliance with Data Leak Prevention Policies to detect and take necessary action against an unsanctioned use.
- Control and Secured Entry Point for advanced security
A Roaming user, once out of the office environment is a major source for a data leak when not under the organization's network. Combining enterprise cloud, the organization can now enforce all communication to be routed through the HO firewall so as to protect from any intentional or unintentional data leak.
- Restrict Personal Use:
Now monitor and control the use of all non-business application and increase productivity. The Data Leak Prevention allows setting of policies to restrict the use of personal email and social media ID and allow only corporate logins. This looks beyond the traditional approach of blocking website and allows the use of useful applications and social media while controlling the use of it with complete visibility.
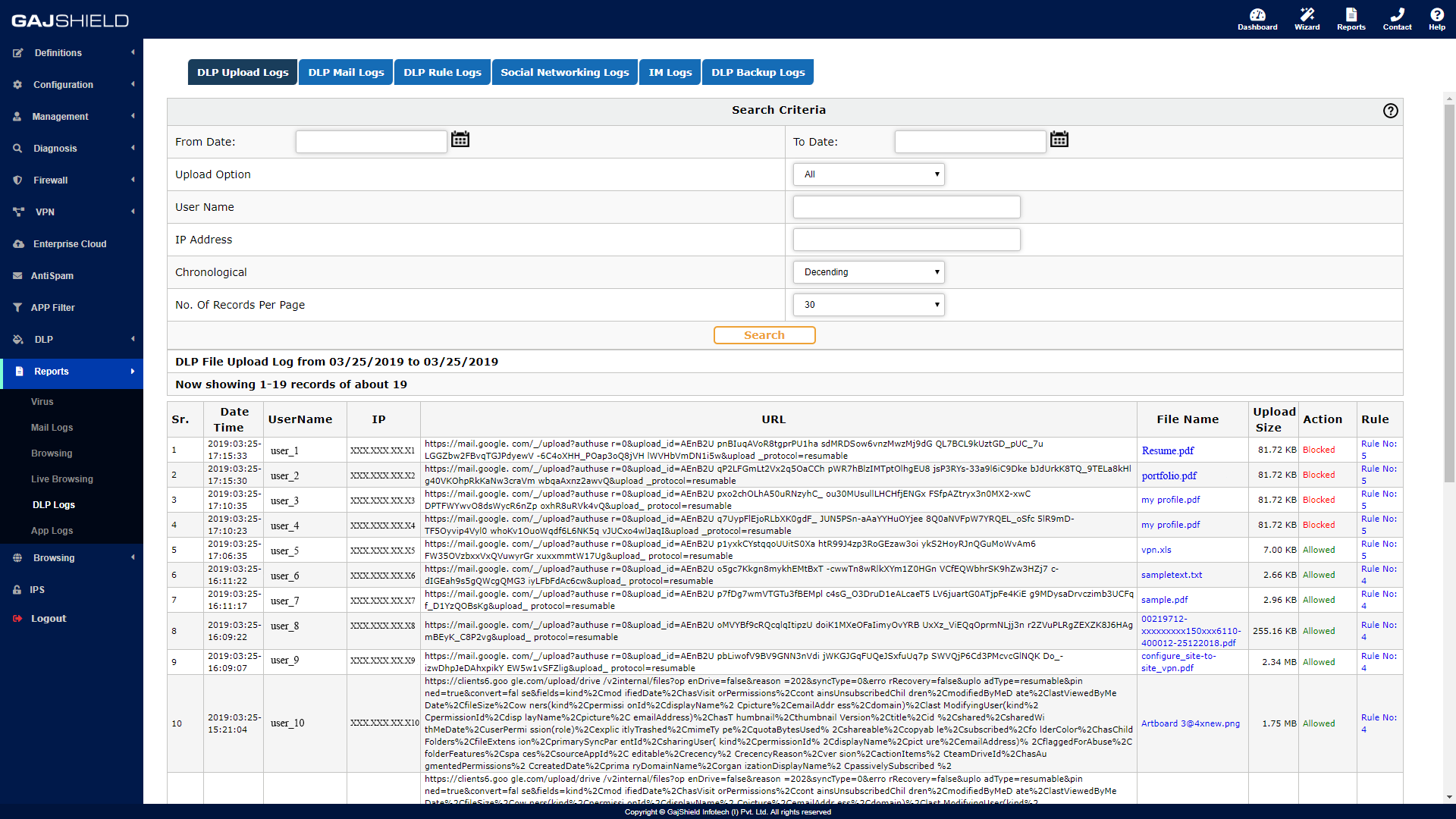
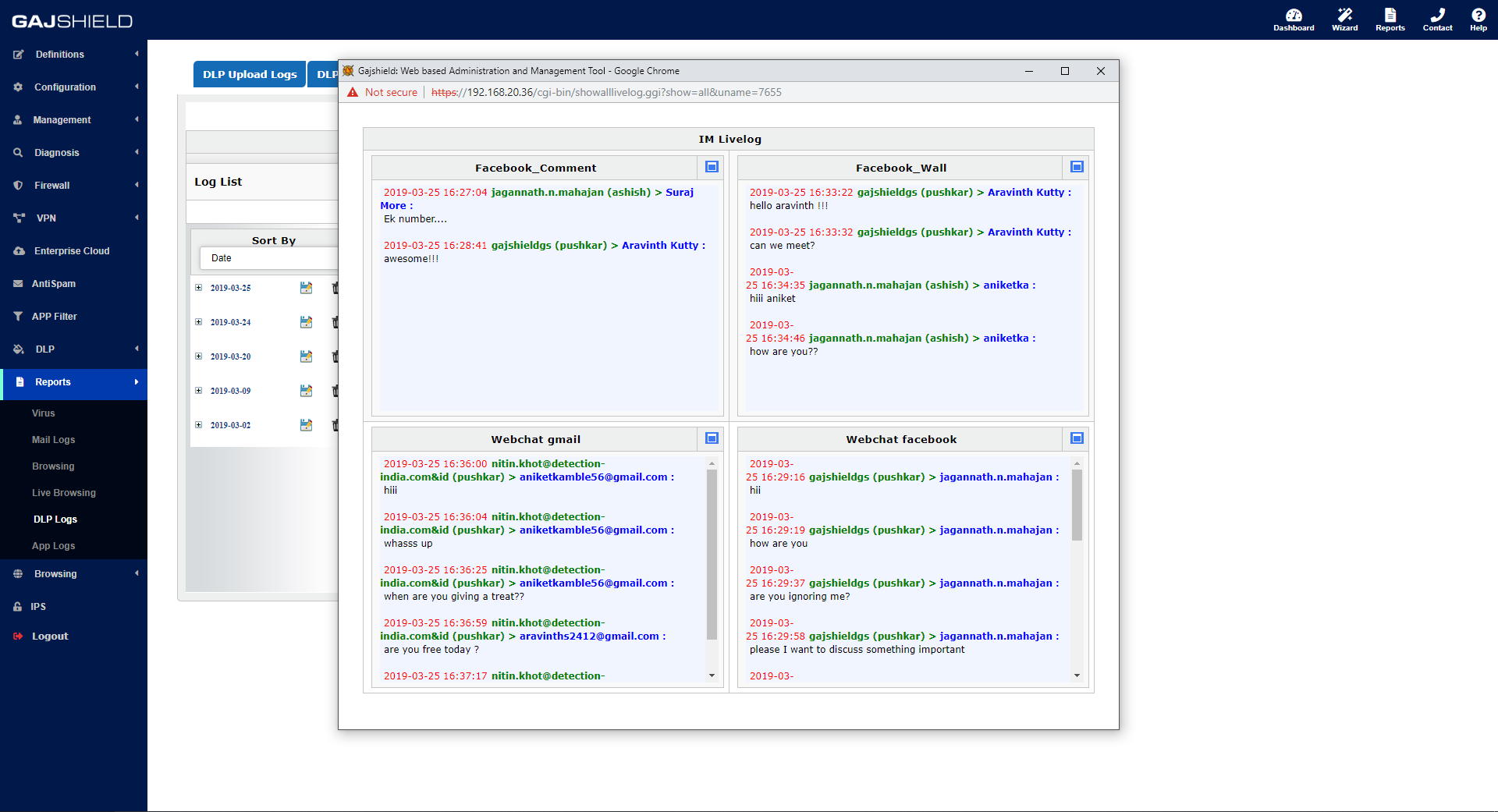
UPLOAD LOGS
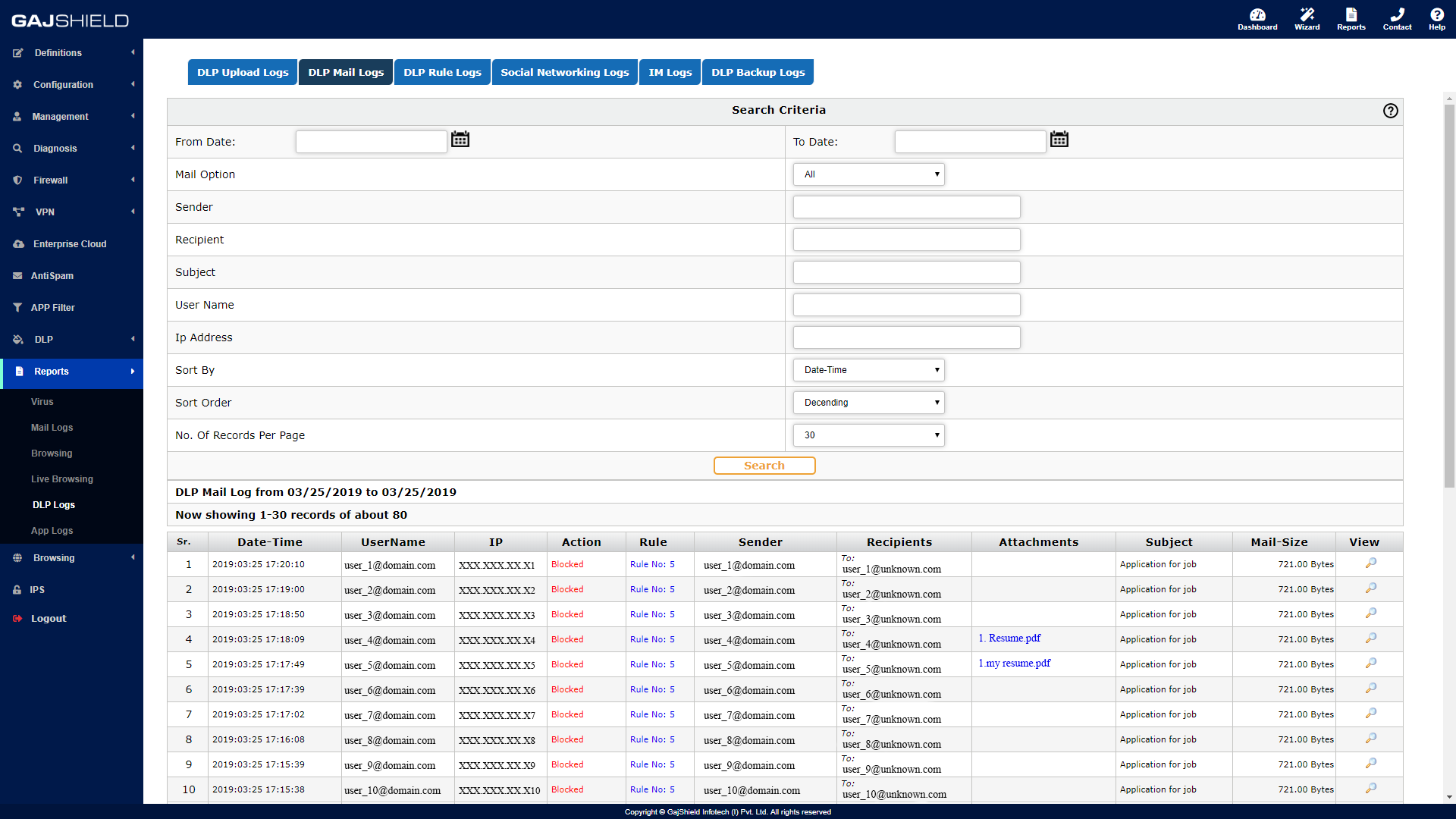
MAIL LOGS
SOCIAL MEDIA LOGS
Why is Data Leak a Concern? This is what customers are telling us about Data Leaks.
- Loss of Sensitive Information - "I don’t know how we can control data from being sent in email or uploaded to the Web."
- Inadvertent Misuse - “Most of our policy violations and information breaches are accidental!"
- Collaboration Risk - "I think some of my employees are posting and sharing confidential information on Social Networking Site like Facebook."
- Context-Sensitive - “My current Data Leak Prevention System causes a lot of false-positive and block data as it is unable to understand the Web application.”
- In-depth Visibility - "Need in-depth visibility on the sensitive data that my employees are uploading. Would be wonderful, if it could give this information in a readable format."
- Data Leak outside Network Perimeter - "What happens when my employees carry their laptop while travelling. Need to control and prevent leaks even when they are out of office.”
Data Leak Statistics
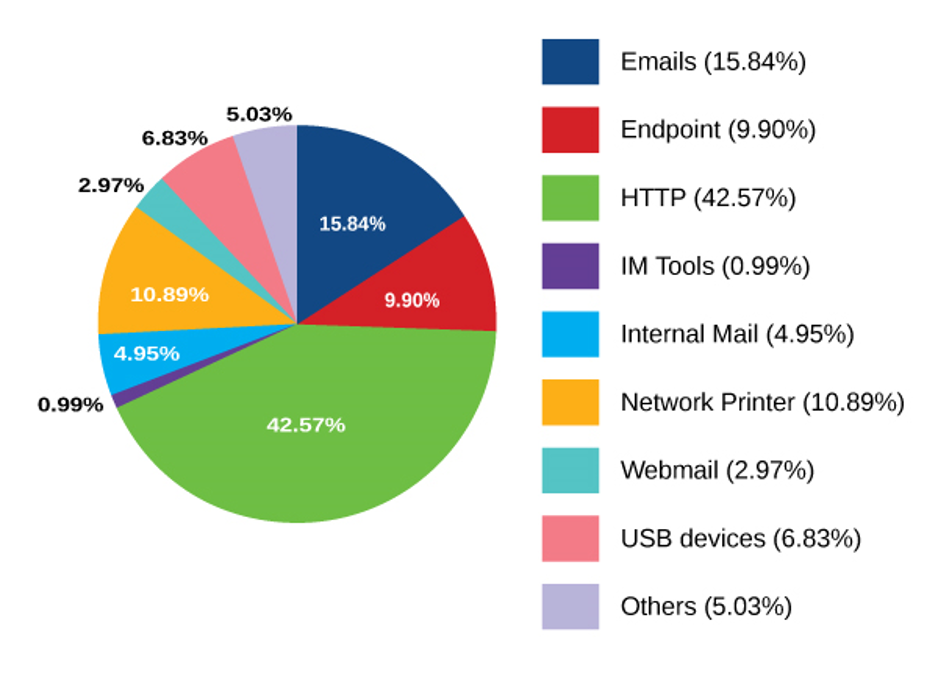
More than 68% of data leak happens through Web and Email and GajShield unique ‘Context Sensitive Data Leak Prevention’ help prevent data leak through these channels.
GajShield’s Data Security Firewall Context based Data Leak Prevention enables to control and mitigate leak of information:
GajShield’s context-based Data Leak Prevention system understands web application/cloud applications by creating context which helps an enterprise to set up policies based on the web application instead of IPs, Usernames which have no relevance to the above application. GajShield firewalls provides visibility to the cloud applications used by an enterprise and also by managing and controlling these applications
GajShield Firewall's Data Leak Prevention and CASB features:
- Detection and Prevention of data leaks
- visibility on the applications used and not just the ports or protocols.
- Monitor and block files being uploaded on the internet with details of the application used and the user who used to upload this file.
- Set policies to monitor/block data leaks via Email, File upload and Chats.
- Set policies to allow read only access to corporate email/social networking.
- Monitor IM & Web chats and block content.
- Set policies based on users, groups.
- Set policies based on application context.
- Schedule DLP policies, for example, you may want to allow certain files after a particular time when this information becomes public.
- Get detailed information of outgoing data on internet from your network.
- Detailed Data Upload/Download Logs, File sharing, email and social media logs
- Complete visibility of data going through encrypted HTTPS traffic.
- Powerful DLP Engine sense data on filters set in DLP polices for a granular analysis.
- Economical cost of ownership.
- Monitor & Block unwanted applications like P2P, Open proxies.
- Easy to configure and integrated into single firewall policy window.
- Standard data leak templates provided to quick setup your DLP feature on GajShield firewall.
- Inspects and helps monitor and control applications like G-Suite, Gmail, Yahoo, Rediff, Office 365, Sify, Google Drive, 4shared, Sky drive, one drive, drop box, media fire, box, facebook wall-message-forum post-comment-note-event, WebChat: msn, yahoo, gmail, facebook, IM-chat: yahoo, jabber, msn, gadu-chat and others.
FAQs
Question: Can I block personal email logins and allow only corporate login using DLP in my organization?
Answer: Yes, using GajShield’s DLP, you can set policies wherein a user is allowed only corporate logins and personal login attempts will be blocked
Question: I want to provide just read only access for the web mail where users should not be able to send any mails out. Can DLP do that?
Answer: DLP enables security managers to set policies to allow read only access to corporate emails/social networking.
Question: I want to block all the mails that are not “cc”ed to Head of the department. Can DLP do that?
Answer: You can setup policies based on “From”, “to”, “cc”, “bcc”, subject of gmail and other such Cloud applications. GajShield also provides BYOD (device) and UserSense(user) information.
Question: Can I restrict the file format to allow only document files to be sent?
Answer: Using DLP, one can easily set restrictions on the type of file that should be allowed to be sent. If any restricted file is sent, a notification is sent to the administrator with complete visibility of the file being sent.
Question: Can I monitor my employees Facebook chats and comments?
Answer: Not just Facebook chats or comments but DLP also provides a global visibility through comprehensive and flexible reporting.
Question: Can I set a limit on the size of attachments that are sent out from my network?
Answer: Yes, DLP does very much allow you to set a cap on the size of attachments that are attached or are been sent out.
Question: Does GajShield DLP inspect SSL traffic for Web and Email traffic?
Answer: Yes, GajShield inspects the SSL traffic for both Web and Email (SMTP SSL/TLS & STARTTLS)
Question: Can GajShield DLP block file uploads to DropBox/GDrive?
Answer: Yes, using policies, GajShield’s DLP can effectively block file uploads to DropBox/GDrive and other such applications.
Complete Visibility
Gain Deep Dive into Data Context of Application
It has been evident and have become a thumb rule for cybersecurity to have visibility on things we want to protect. Simply, you cannot protect that you cannot see. While Cybersecurity is never a static, one-time initiative but an ongoing process that should always be top-of-mind for CSOs, CIOs, and other IT leaders. To that end, technology and security leaders should always have access to information regarding the security of their enterprise networks possible only if they have visibility not only on their network but beyond just the network. In fact, not just the leaders but even employees need real-time Data visibility to report any damage to or illicit use of the organization’s Critical Data. And ensuring enterprise-wide Data visibility should be a priority even if the organization uses the most cutting-edge cybersecurity tools and technologies. That’s because cybersecurity systems, while generally being effective at keeping bad actors out and sensitive data in, cannot keep your Data protected all the time and from all threats if it does not have visibility. There can always emerge newer forms of threats that may require the immediate attention of an enterprise’s cybersecurity personnel and leaders. And the time it takes between a threat’s incipience and the cybersecurity team’s awareness of it can be the difference between security and enterprise-wide mayhem.
The most compelling reason as to why data visibility is a must for data security is simply that it is impossible to protect what you can’t see. An enterprise data must be monitored everytime it exists the organization. That means having real-time knowledge of:
- Every piece of information that is transmitted to, from, and within the organizational network.
- The source and destination (E.g. URLs, email IDs, body content, subject, attachments, content of attachments etc.) of every inbound and outbound communication.
- Gains visibility on internet activities of computer devices used by the enterprise, which includes all the laptop computer devices used by employees from other remote locations.
At GajShield we understand how enterprises workforce make use of data in their day to day activities and the importance of data for business continuity. These data are very useful and if fallen in wrong hands, can result into disastrous situations. To protect these data and prevent data exploitation, one must have visibility beyond just the traditional Layer 7 to understand i.e. understand of further contextual data that is associated with the identified application in use.
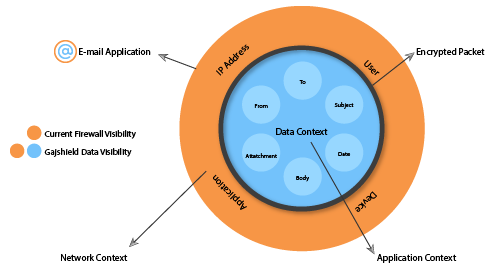
GajShield Data Security Firewall uses Contextual Intelligence Engine and Combines it with advanced reporting capabilities of GajOS: Bulwark for Enterprises to augment their traditional layer 3 (network level) security with a layer 7 (application level) security solutions and deep dive past than just the layer 7 into Data Context to create contextual information. GajShield Data Security Firewalls perform Data Layer inspection with the help of Contextual Intelligence Engine to create data context and analyze a broader range of parameters with greater in-depth data layer visibility, extending the visibility to more data like Email ID, Sender ID, recipient ID, CC mentions, Subject, Mail Body, Signature, File Content, downloader, uploader etc. across web traffic and SaaS applications to identify abnormal behaviors that may indicate potential cyber and data threats.
Analyzing these parameters, the Data Security Firewall determines the safety and legitimacy of communications & transactions and takes necessary actions to prevent data exploitation and this capability can is useful in mitigating the impact of a zero-day attacks.
Using GajOS Bulwark, GajShield Data Security Firewall provides
- Complete visibility of the applications and bandwidth used.
- Complete visibility of evasive applications like P2P and Skype application.
- Complete insight on :
- Content upload via Web uploads ex: webmail, Social networking sites, Blogs, Instant Messaging, Mail.
- Content sent through email.
- Content sent through Instant Messaging.
- Comprehensive reporting on :
- Top Internet Users.
- Top Bandwidth Users.
- User/Group Activity.
- Application Traffic.
- P2P Usage.
- URL/Category Usage.
- Total Internet Traffic.
- Application Traffic, Total Traffic, Application set and application detail.
- Web Browsing by URL, Category and User.
- Trend Analysis of applications, users and bandwidth.
- Current, Daily, Monthly, Yearly reports And much more.

BYOD
A Solution to Monitor and Control Devices Brought and used by Employee
BYOD is increasingly becoming more popular, not just nationally but also globally. A recent survey has indicated that about 28% of the global workforce used personal devices for official purposes and the mobile workforce worldwide is expected to rise from the current 1.45 billion to 1.87 billion by 2022. With such a remarkably increasing popularity of the Bring Your Own Device (BYOD) program, it becomes an organization’s responsibility to manage the various multifarious devices that the employees perform their work related tasks through and at the same time protect the data from being compromised. GajShield’s BYOD management gives the enterprises a complete solution by providing them with the ability to set policies and restrictions to keep the data safe and seamless.
The rise in the occurrence of data leaks can be, in part, attributed to the propagation of enterprise mobility and the Bring Your Own Device (BYOD) culture, without due attention directed towards the associated data and cybersecurity risks that emerge. Businesses, in an attempt to increase employee productivity and to save on heavy infrastructure costs, are encouraging employees to use their personal devices for work. As a result, it is becoming harder for the enterprise cybersecurity team to monitor every device and implement a uniform data security policy across all devices. This results in users using their devices to share information outside the organization accidentally. Even if an enterprise uses email security to prevent employees from leaking information, users can use other applications using their personal devices to share information.

Using a Data Security Firewall solution with BYOD protection can ensure that data security policies are applied to all devices, regardless of differences in their manufacturers or operating systems. It prevents users from sharing confidential data to those outside the organization. Using a BYOD security system also prevents suspicious and risky applications from running and leaking critical enterprise data without the knowledge of users.
GajShield’s BYOD Policy works effectively on its Data Security Firewall series. GajShield’s BYOD feature aims to enhance the UserSense engine in the popular DC and NU Series to inspect, detect and monitor the traffic and control the devices being used by employees. BYOD management is able to identify the end point including whether it is coming from a mobile device or a desktop. This information greatly helps the enterprises to set up different BYOD policies limiting the access to internet or mobile applications as per their requirements.
It often happens that employees are allowed to bring in devices which are not controlled by the enterprise. Many of these devices have varied Operating Systems like Android, iOS, Windows, etc. and the chances of malicious apps been downloaded on these devices is very high. These devices can compromise the enterprise network with unaccounted traffic. In order to overcome this issue, GajShield’s Data Security Firewall.
Uses and Object-Oriented Policy security management that allows enterprises to take various steps to step up the security of their system.
Enterprises can block access to critical servers in DMZ to BYOD devices, they would be able to setup Data Leak Prevention solution and apply data security policies that would help them to monitor and block all data uploads from these devices, furthermore, risky applications with possible data leak threats could be easily blocked
GajShield also helps enterprises to set up policies to limit access to the internet (based on time) from these devices and control and limit the bandwidth used by these devices. All the BYOD devices can be redirected to non-critical internet links so that the business applications are not affected.
By incorporating these security features, enterprises can avail the advantages of lesser investments in hardware as employees would bring in their own devices and GajShield’s BYOD would ensure security as well. For employees, it is a win-win situation as well as it provides them with flexibility and technology familiarity as employees tend to be familiar with their own devices.
KEY FEATURES:
- Block access to critical servers in DMZ to BYOD devices
- Setup Data Leak Prevention policies which monitor and block all upload from these BYOD devices
- Block risky applications which can lead to data leak from BYOD devices
- Setup policies to limit access to internet from these devices
- Control and limit the bandwidth used by these devices
- Control and limit unauthorised access
- Limit access to internet based on time. (Education institutes do not want students to have access to internet during class hours)
- Redirect the BYOD devices to non-critical internet link so business applications are not affected
- Individual user wise report based on BYOD devices.
GajShield SOLUTIONS
Centralized Management SystemThe GajShield Sangam is a Centralized Management System dedicated to manage GajShield’s Data Security Firewall all at one place. Sangam enables network admin to manage distributed network of GajShield Data Security Firewalls, managing all aspects of device configuration, push data security policies, global security policies, view all firewall traffic, and generate reports — all from one central location using a single console.
Single Platform for Security.
GajShield Sangam provides administrators of simple or complex network environments with a powerful, intuitive interface to centrally manage multiple GajShield Data Security Firewall appliances including network policies, URL filtering, Data Leak Prevention, Application Filtering, IPS, Gateway Antivirus, Gateway Anti-spam, ISP Failover & Load Balancing and software updates.

One Point Reporting:
Sangam offers Real-time visibility of threat summary and trends. its powerful reporting allows network and security manager to manage and view complete security report from a single management platform.
Centralized Management:
Sangam offers a unified platform for managing all the firewall in the organization’s network. It offer the Ability to individually configure advanced options of the firewall, Ability to define Firewall, IPS, URL Filtering, DLP, Application Filtering, Gateway Antivirus, Gateway Anti-spam, ISP Failover & Load-balancing policy implementation from central offices, functionality to add Groups and configure multiple firewalls together at the same time, feature to retrieve all the firewalls health status in a single dashboard, Intuitive and comfortable UI, ability to work with Pseudo Interfaces/Hosts/User Groups and be independent from firewall constraints like IP addresses and usernames, functionality to take firewall backups and save them in a central location, Add new firewalls to a group to make it act as the one amongst the group, Have the server auto-synchronize all the firewalls at regular intervals, etc.
Single-Touch Deployment:
Single-Touch Deployment. GajShield’s simplified deployment capabilities allow enterprises to ship unconfigured GajShield NGFW appliances to each remote site. When plugged in, the appliance connects to the service in Centralized Management Service Server. Within seconds, the server authenticates the remote device and connects it to a Central Management System for easy policy deployment.
Advantages
- Centralized Policy management
- Easy operations with minimum learning curve
- Flexible deployment
- Consolidated Network and threat visibility
- Reduced operational cost
- Allows grouping of security appliances
- Create policy templates, which can be re-used.
ATP - Zero Hour
A Zero Hour Malware Protection with Intelligent Sandboxing
The Data Security Firewall uses an Advanced threat protection is a solution that helps keep zero-day and advanced threats away from entering an organization’s network. These threats are usually engineered to be disguised as good traffic and evade security measures used by the target organization. These can be a malicious file, URL or a constructed mail for well a planned attack.
GajShield’s Intelligent Sandboxing technique identifies malicious files and sandboxes it in a virtual environment, away from the organization’s network to traps the injected malware.
The ATP combined with advanced Machine Learning capability that finds outlier to identify suspicious traffic for further process by the security engines for preventing zero-day threats and keeping them away from the network. Today's viruses, Malwares, Worms and Trojans target the primary weakness in anti-virus technology: the time it takes for new signatures or heuristics to be developed and distributed. GajShield Next Generation firewall appliances, integrates Zero-Day Virus Outbreak Protection to shield enterprises in the earliest moments of malware outbreaks, and right through as new variants emerge.
GajShield zero-day protection overcomes the newer security issues witnessed, in which large quantities of Trojans and other viruses are being missed by traditional signature-based and heuristic antivirus engines increasing the risk for organizations.
Advantages:
Intelligent Sandboxing:
GajShield’s Intelligent Sandboxing service is a cloud-based sandbox designed to discover unknown threats such as ransomware at the gateway, by creating a virtual environment away from organization’s network and running the suspicious file to identify previously unseen malware and threats. It analyses executable programs (PE), JAR, APK, DLL, PDFs and MS Office files etc. (50+ types). It has support for multi-operating systems including Windows, Android, Mac OS and Linux. An organization can decide which files it would like to exclude from sandboxing based on file type, name, sender and recipient.
GajShield Threat Lab:
GajShield Threat Lab stores a database of all Proactive virus and malware detections, bad IP addresses, domains and URLs. At the GajShield Threat Lab, a database of real-time spam outbreaks is collected and compiled and maintained, through consultation with global Internet Service Providers. Patterns are analyzed, categorized, and cross-matched using algorithms, run to optimize the detection of repeating patterns and their sources. This database, containing approximately over six million signatures, is continuously updated with more than 30,000 new unique signatures added hourly. GajShield Threat Lab uses honeypots, sensors deployed across the internet which provides early warning of cyber attacks. Machine learning is used to crawl the internet to identify malicious sites. The cyber threat intelligence (Indicator of Compromise list) which consists of bad IP addresses, domains, URLs, file hash (md5/sha256), malware signatures, spam outbreak signatures which are generated by GajShield Threat Lab, is fed into each security component of GajShield NGFW. With the release of GajShield DSF Bulwark firmware, GajShield firewalls intelligently identify various attempts to compromise and alert the administrator in real time. Advance DSF engine monitors traffic in real time and using the IOC list is able to identify attempts to compromise database servers, unauthorised access to Windows or Linux servers, suspicious traffic or even attempts to leak data out of your network.
Signature – Independent Protection:
Signature-independent protection is an essential complement to traditional AV technologies, security experts agree. By proactively scanning the Internet and identifying massive virus outbreaks as soon as they emerge, GajShield's Zero-Hour (Zero-Day) Solution provides just that: proactive virus blocking that is effective and signature-independent.
Gateway Defence:
GajShield Firewall sits at the gateway and acts as the first point of encounter to all cyber threats. Its proactive security helps in defending cyber-attacks, real-time. It deals with the threats at the gateway, keeping threats away from the organization’s network thus, maintaining a cleaner network environment.
Immediate:
GajShield provides enterprises with proactive virus detection they need to close the early-hour vulnerability gap during which millions of users are infected. GajShield's proactive virus detection capabilities ensure users' protection hours before signatures are released.
Artificial Intelligence and Machine Learning:
AI and ML-based cybersecurity solutions will become a necessity in the future of cybersecurity as traditional means will become incapable of mitigating the risks posed by ever-evolving malware, hacks, and other types of cyber-attacks. AI-based self-learning applications will become a standard part of cybersecurity teams’ toolkits that will ensure continued protection against evolving risks.
Proven:
Robust and inherently immune to emerging foiling attempts, GajShield has a proven record of being one of the highest performings among proactive virus control solutions. GajShield's Zero-Hour Virus Outbreak Protection is powered by GajShield Threat Lab, which has a track record of protecting millions of users globally.
Features:
- Ransomware Protection
- Malware Protection
- Real-time inspection & protection from unknown threats through proactive/stream mode
- Deploy signatures to the firewall when a file is identified as malware
- Analyses archives like zip, tar, gzip, 7z, rar across all operating systems.
- Analyses many different malicious files irrespective of its size (executables, office documents, pdf files etc.) as well as malicious websites under various operating systems like Windows, Linux, Mac OS and Android.
- Trace API calls and general behaviour of the file and distil this into high-level information and signatures.
- Threat analysis on dashboard
- Analyse network traffic, even when encrypted with SSL/TLS.
- Perform advanced memory analysis of the executable programs to identify and detect potential malicious files.
- Recurrent Pattern Detection of unknown malware through emailing protocols
- Multiple spam classification
- Independent of Content, Format, Language
- Real-time Blacklist (RBL), MIME header checks
- Filter based on message header, size, sender, recipient, subject line tagging
- Zero hour Virus Outbreak Protection
- Anti-botnet security
Page 3 of 17
