Secured Guest Management
A Solution to Monitoring and Control Network & Internet use by Guests
Guest visitors to an enterprise, hotel, colleges or even public hotspots might need access to the internet during their stay. The challenge faced by IT Managers is how to control and limit internet access of guest users without having to configure the guest’s desktop and yet have a solution which is cost-effective and easy to manage. IT Managers would need a solution which would provide a positive visitor experience without compromising the security of an enterprise.
In providing internet access which could be for a day or even weeks during the stay of a guest, another challenge IT Managers face is creating temporary user IDs for guests. Maintaining such a large changing list of users is a tedious job for an admin. It is also difficult to apply access restrictions to these users, as users database is frequently changing/getting updated.
Solution
GajShield’s SECURE GUEST INTERNET MANAGEMENT SYSTEM fulfils all the above requirements, yet it is simple to manage, scalable and cost-effective too. The system helps to manage guest users, whether wired, wireless or even using mobile for internet access. Its auto expiry feature makes it easy to manage large sets of guest users. Its reporting system gives in-depth usage information and helps to identify any misuse by these users.
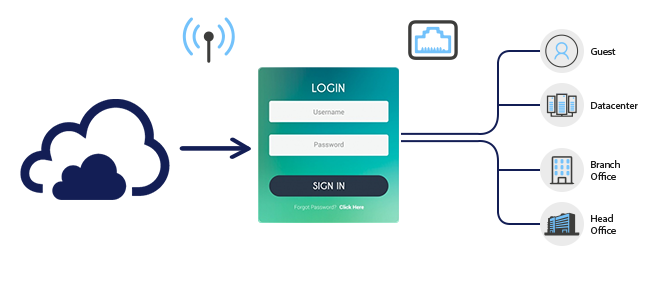
With this system, the IT Administrator can create guest users manually or provide an option to guests for self-registration. GajShield's Data Security Firewall provides user credentials via SMS which expires after a pre-configured / pre-defined time. Security policies can either be set for the guest group or can be defined for an individual user.
By terminating the guest network on a separate port of GajShield Firewall, enterprises can also control and limit guest users access to a corporate network.
Prerequisites
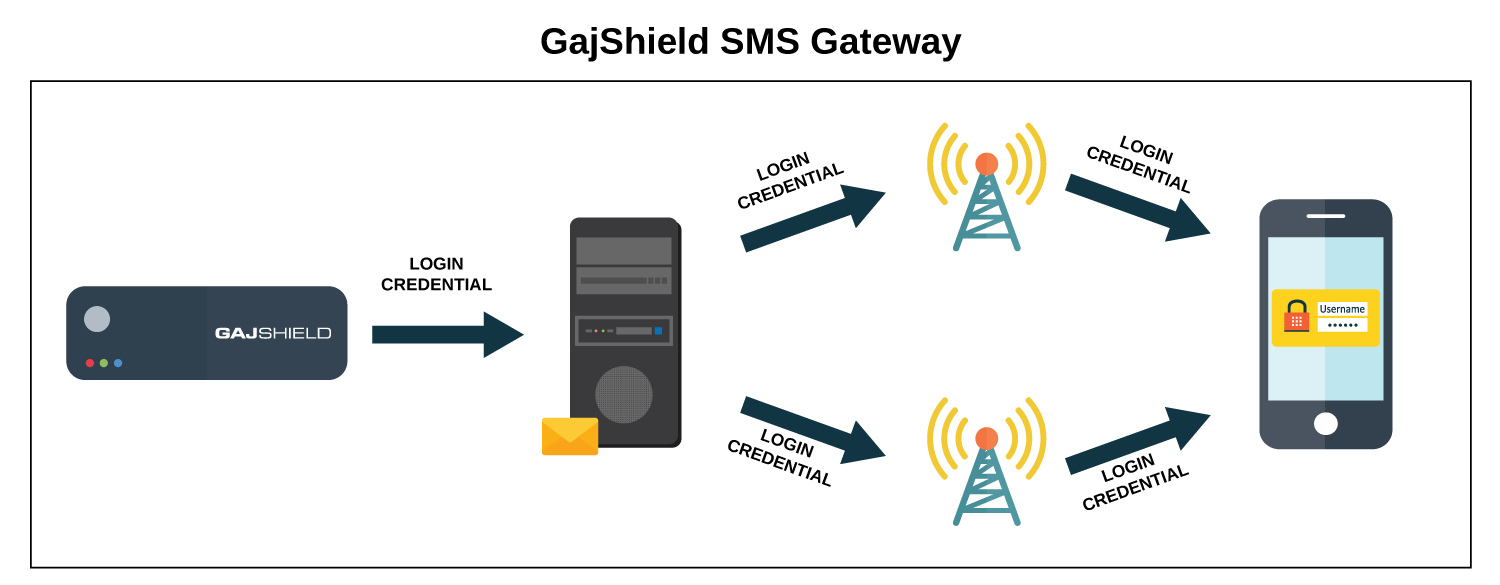
SMS Gateway
User credentials can be either sent via email or using SMS. To send Username and Password via SMS, the organisation will have to be registered with an SMS Gateway service provider. GajShield Firewalls come with pre-configured API parameters for various service providers. For service providers not listed in GajShield, the API parameters would have to be obtained and configured on GajShield Firewalls.
Features:
GajShield Guest Management System simplifies administration of guest users, a tremendous benefit for IT staff that will have a very limited workload in the daily operation.
Guest login portal
This is the interface used by guests and gives the very important first impression of a company. This portal is customized according to the organization and is a powerful branding as well as an information delivery tool. Guests connecting their laptop or smartphone to the internet will immediately be redirected to this portal. They will then log in to access the Internet.
One of the more popular guest provisionings flows is guest self-registration with SMS activation:
- The guest registers and enters his/her mobile number at the guest login portal.
- A one-time access code/ username and password is delivered to the mobile phone via SMS (Short Message Service).
- The guest activates the guest account using a provided username and password.
The use of activation through the mobile number enables traceability of the guest’s activity in the network as the identity of the guest will be automatically validated through the mobile subscription.
Guest Administration
This works as a control centre for IT staff. The Firewall Management System helps in configuring security policies for guest users along with configuring SMS gateway, guest portal and registration. It also provides a detailed reporting system built with intelligence to identify anomalies and misuse of policies.
Along with the above features, GajShield solution also provides:
- Create Guest Users Manually or User can register themselves through the Registration process
- Add Guest Users in bulk (through CSV upload)
- Delete Multiple Guest Users manually or enable Auto-Delete (automatically deletes user on expiry of validity)
- View Guest User Registration and Auto-Delete Logs
- Option to resend Guest User Credentials on SMS
- Create Group(s) of Guest Users
- Apply Security Policies (like URL, DLP, Application Filter Policies) based on Guest User(s) and/or Group(s) of Guest Users
- Apply Bandwidth Capping/Queue on Guest User(s) and/or Group(s) of Guest Users
- Apply UserSense Sessions and Authentication Schedule (Time Schedule) based on Guest User(s) and/or Group(s) of Guest Users
- Apply Bandwidth and/or Time Quota on Guest User(s) and/or Group(s) of Guest Users
- Can route traffic of Guest User(s)/ Group(s) of Guest Users through different ISP(s)
- Can apply BYOD restriction on Guest User(s) and/or Group(s) of Guest Users
Multi-Wan Management
Control & Distribute Traffic Across Multiple Internet Links
Internet connectivity is at the heart of your business. Many businesses have multiple Internet connectivity (multi wan). Enterprises rely on the Internet to run their mission-critical business applications which drive their productivity and profits. It is expected that Internet connectivity to be highly reliable and always available. If the physical connection or the ISP goes down, organisations vital link to the Internet also goes down which affects business.
Revenue, customer satisfaction, partner relationships and employee productivity, all are at stake when internet link goes down. Internet outages impact an organisations email, websites, applications or VPN traffic.
GajShield’s ISP Failover & Load Balancing allows enterprises to control and distribute traffic across multiple internet links.
GajShield policy-based Failover & Load Balancing enables enterprises to distribute important applications over more robust internet links and less important applications over broadband connections as well as provide redundancy in case one more internet links are down.
Multi-Wan - ISP Link Redundancy – Failover
GajShield Multi wan or ISP Failover manages the traffic while providing valuable failover capabilities. That way if an internet link fails, GajShield senses the disturbance and redirects traffic to one of the working internet links.
GajShield checks the health of the available internet connections, continuously checks the status of all the internet links, detecting failures in real-time and automatically redirects the traffic to the operational internet links to guarantee full availability.
Customer can choose a granular option to define the primary internet link and multiple secondary internet links for each different service. For example for email the primary link could be ISP1, the secondary could be ISP2 and third link could be ISP3, while for FTP the primary could be ISP2, the secondary could ISP3 and third, could be ISP1.
Multi-Wan - ISP Load Balancing
GajShield Multi wan or ISP Load Balancing weighted round-robin method and hence it distributes the traffic across multiple internet links and provides the flexibility of utilizing the total bandwidth of all the internet links preventing bandwidth bottlenecks while minimizing the cost of inefficient bandwidth utilization. At the same time, GajShield detects any failure of the internet link and dynamically load balances the traffic over the available or Live internet link.
Integrated reporting and Alerts
GajShield reporting provides current, daily, monthly and yearly reports and trend analysis of ISP utilization, what applications are being used through the ISP’s and which user is using the ISP. Enterprises can determine misuse or abuse of internet links by applications and users to effectively utilize the internet links available and to make informed decisions related to bandwidth purchase and management. GajShield Alerting mechanism sends email alerts to administrators keeping them informed on the link outages facilitating rapid troubleshooting.
Features of GajShield Multi-Wan Management:
• Service-based ISP load balancing or failover.
• Both Failover and Load Balancing can be set up simultaneously.
• Load balances traffic based on weighted round-robin distribution.
• ISP Failover automatically shifts traffic from a failed link to a working link.
• Automatic traffic tailback when failed ISP comes. up
• Zone-based failover.
• Customized NAT on failover.
• ISP failover and tailback notifications on email.
Email Security
Protect Against Latest Email Borne Threats
Email being the primary means of official communication, has become a gateway for threats for a lot of companies. Companies of all sizes face this daunting challenge. While email threats move fast, and malicious files look more like normal files that are often used for communication.
GajShield Email Security enables enterprise users to communicate securely and protects them from latest email-borne threat vectors like ransomware, advance malware, spam, phishing and data leak using its unique Contextual Intelligence engine with multi-layered approach to security.
APPROACH
- GajShield Threat Lab
Proactive virus detection, Robust and inherent immune system that integrates Zero-Hour (Zero-Day) Virus Outbreak Protection to shield enterprises in the earliest moments of malware outbreaks, and right through as new variants emerge. By proactively scanning the Internet and identifying massive virus outbreaks as soon as they emerge, proactive virus blocking is effective and signature-independent.
At the Threat Lab, a database of real-time spam outbreaks is collected and compiled and maintained, through consultation with global Internet Service Providers. Patterns are analyzed, categorized, and cross-matched using algorithms, run to optimize the detection of repeating patterns and their sources. This database, containing approximately over six million signatures, is continuously updated with more than 30,000 new unique signatures added hourly.
- Contextual Intelligence Engine:
All new contextual intelligence engine for ultimate visibility and better security. The Contextual Intelligence Engine helps in creating context of the mail application beyond just the traditional context. It analyses the usage of the application and creates context by deep diving into granular details like: Address of Sender, Address of Recipient, Subject, Mail Content, Attachments, Signature, etc. for better and informed security with advanced visibility of mail services.
- Recurrent Pattern Detection:
At the heart of the GajShield’s Mail Security is its powerful, Recurrent Pattern Detection, a spam engine that identifies spam patterns regardless of content, format, or language. By immediately detecting new attack patterns, and maintaining a database of spam outbreaks, the RPD engine identifies the quantity and the speed of the distribution of spam.
- Network Sandbox:
An Intelligent Network Sandbox solution that has anti-evasion capability for protection against malware that understands and detects a virtual environment. With the ability to sandbox various file types and embedded URLs, our intelligent sandbox inspects content that a traditional signature-based antivirus cannot identify as malicious and categorise accordingly.
HIGHLIGHTS
- Global threat intelligence processing over 25 billion transactions daily
- Block ransomware, spam, phishing and malware attacks before it reaches your infrastructure
- Advanced malware protection using machine learning techniques to model trusted email behaviour
- Advanced threat protection using Contextual Intelligence, Recurring Pattern Detection, reputation scoring and file sandboxing
- URL-related protection and control using scanning of URLs in emails based on their category and reputation
- Combines rapid Domain Message Authentication Reporting and Conformance and forged email detecion using DKIM and SPF to protect against BEC attacks
- Protect sensitive data with integrated Data Leak Prevention solution
- Seamless integration with GajShield Archiving solution Simple to manage and configure using a Web-based Administration In-depth reporting offers single view for comprehensive insight across your organisation
- Simple to manage and configure using a Web-based Administration
- In-depth reporting offers a single view for comprehensive insight across your organisation
FEATURES
Multi-layered Protection:
- Scrutinises IP, domain of mails
- Reputations check and validation
- Bounce history, address authentication
- DMARC and DKIM checks
- Analyse message and content structure
- Analyse Image, Digital signature, keywords in context
- Scan embedded URIs
- Categorizing
Data Leak Prevention:
- Deep packet analysis
- Restrict content sharing
- Easy policy implementation
- Unique group mailing policies
- Protect critical data
Gateway Anti-Malware
- Powerful and Real-Time protection from Virus outbreaks
- Scans HTTP, HTTPS, FTP, POP3, SMTP & SMTPS traffic
- Detects and removes viruses, worms and all kinds of malware.
- Instant identification of virus-infected users
- ZERO Hour Virus protection
- Spyware, Malware, Phishing protection
- Automatic real-time Virus update
- Complete protection of traffic over all protocols
- Last virus update definition
- Complete report
Advanced Threat Protection:
- Advanced Email Protection.
- Anti-Virus.
- Anti-Spam
- Advanced Intelligent Sandboxing.
- Complete Mail Analysis
- Deep Mail Inspection
Gateway Anti-Spam
- Scans SMTP, POP3 traffic for spam
- Detects, tags or quarantines spam mail
- Content-agnostic spam protection including Image-spam.
- Preemptively stops sophisticated threats like phishing, pharming, zombie attacks & supports
- RBL lists
- Enforces black and white lists
- Real-Time protection from emerging threats
- Language, content, format & signature independent spam prevention
- Detects phishing URL in emails
- Quarantine Spam Mails
- Mail Archiving
SD-Wan
A Modern Networking Solution for the Digital World
The speed of business continues to accelerate. Competition is fiercer than ever; customer expectations are higher than ever. Today’s businesses run on applications and rely on connectivity, and when you’re opening up new sites or branches, time is money.
Geographically distributed organizations often have hundreds or even thousands of branch offices connected to a hub or headquarters’ sites. For security reasons, cloud-based application traffic is often backhauled from the branch across expensive WAN/MPLS links to a hub site before being handed off to the Internet. Not only is this expensive, but performance is often compromised due to WAN bandwidth constraints at the branch and added latency from backhauling connections.
A solution is to use direct Internet connection that provides simpler and consistent performance to cloud-based applications. With GajShield Data Security Firewalls, Internet connections become secure and reliable, it helps in augmenting or even replacing the traditional MPLS connections and lower WAN costs.
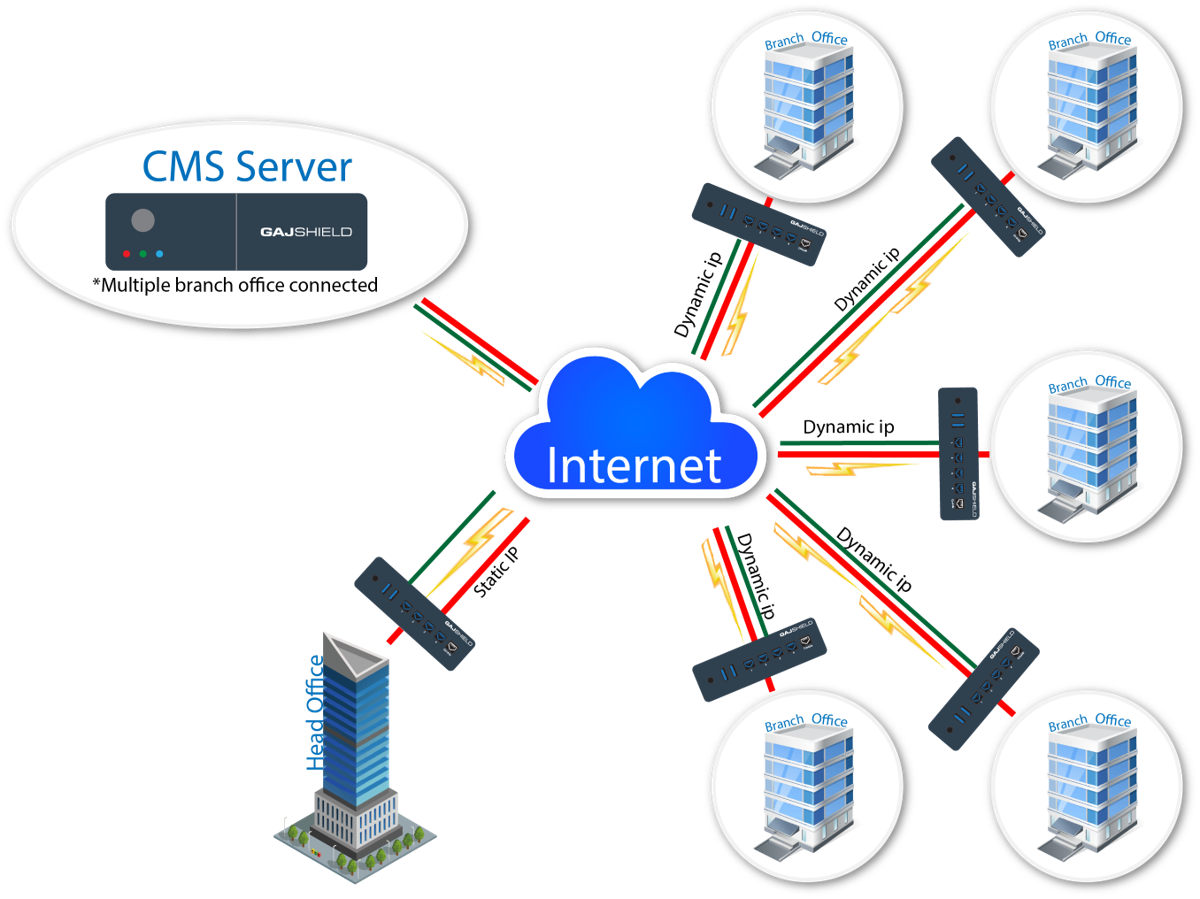
GajShield GS-Branch:
Distributed enterprise branches transitioning to a digital business model have a significant impact on their network. With enterprise users both remote and local directly accessing the internet for cloud and Security-as-a-Service (SaaS) applications, the WAN and access edges are getting more complicated than ever and introduce new vulnerabilities for attackers to exploit. GajShield Firewalls enables customers to converge their security and network access, extending the benefits to their distributed branches. GajShield security device is comprised of GajShield Data Security Firewall, Secure Access using VPN, Anti Malware with Advance Threat Protection to deliver consolidation of branch services for network edge and device edge protection.
Features:
- Centralised policy management
- Easy operations with minimum learning curve
- Flexible deployment
- Consolidated Network and threat visibility
- Allows grouping of security appliances
- Complete threat protection including firewall, gateway anti malware, DLP, application control, intrusion prevention system and URL filtering
- Re-usable policy templates.
Centralized Management System
Quick Deployment:
GajShield’s simplified and easy deployment capabilities allow enterprises to ship unconfigured GajShield Data Security Firewall appliances to each remote site. When plugged in, the appliance automatically connects to the service in Centralized Management Service Server. Within seconds, the server authenticates the remote device and connects it to a Central Management System. The GajShield Centralised Management System is a dedicated network security management appliance, that enables network admin to manage distributed network of GajShield Firewalls, like managing all aspects of device configuration, push global policies, view all firewall traffic, and generate reports — all from one central location using a single console. Multi-path technology can automatically failover to the best available link when the primary WAN path degrades. This automation is built into the GajShield’s Multi-WAN management, which reduces complexity for end-users while improving their experience and productivity.
Benefits
- Lower Cost or Setup and Operation
With the help of Centralised GajShield Security Management Architecture, enterprises can deploy and manage multiple Internet links, you can now augment or even replace MPLS connections with broadband internet services to connect users to applications and lower WAN costs by up to 90%. The ROI is dramatic and immediate.
- Better Performance
GajShield Security Architecture is powered by multi-core architecture which provides faster application steering and unrivalled application identification performance. This includes deep secure sockets layer (SSL)/transport layer security (TLS) inspection with the lowest possible performance degradation.
GajShield’s MultiWAN management helps in routing applications and users over the most efficient WAN connection at any point in time. To ensure optimal application performance, it identifies a broad range of applications and applies routing policies at a very granular level for better end-user productivity.
GajShield’s application engine uses an application control database with the signatures to identify various applications (plus regular updates from GajShield threat Lab). GajShield identifies and classifies applications, even encrypted cloud application traffic, from the very first packet. This can be set to recognize applications by business criticality. Unique policies can be applied at a deeper level for sub-applications. This deep and broad application-level visibility into traffic patterns and utilization offers a better position to allocate WAN resources according to business needs. - Highly Available
One of the goals of high availability is to eliminate single points of failure in your infrastructure. A single point of failure is a component of your technology stack that would cause a service interruption if it became unavailable. As such, any component that is a requisite for the proper functionality of your application that does not have redundancy is considered to be a single point of failure.
High availability is an important subset of reliability engineering, focused towards assuring that a system or component has a high level of operational performance in a given period of time. At the first glance, its implementation might seem quite complex; however, with GajShield it becomes much simpler and it can bring tremendous benefits for systems that require increased reliability.
Better Security
- Data Leak Prevention
DLP identifies, monitors and protects the data in motion on your network through deep content inspection and contextual security analysis of transactions, DLP systems act as enforcers of data security policies. They provide a centralized management framework designed to detect and prevent the unauthorized use and transmission of your confidential information. DLP protects against mistakes that lead to data leaks and intentional misuse by insiders, as well as external attacks on your information infrastructure.
- Contextual Intelligence Engine
Contextual Intelligence Engine is a technology that allows to gain advanced visibility of data transaction over applications that uses network. Context-based security approach is a step ahead from traditional firewall capabilities. Using deep inspection at Different Levels for advanced security, Contextual Intelligence Engine understands the application and its data context. It allows to create a context of Saas applications and understand its usage, much deeper than just the application. Combined with Machine Learning, the contextual intelligent engine helps in finding anomalies.
- Intelligent Sandboxing
An Intelligent Network Sandbox solution that has anti-evasion capability for protection against malware that understands and detects a virtual environment. With the ability to sandbox various file types and embedded URLs, our intelligent sandbox inspects content that a traditional signature-based antivirus cannot identify as malicious and categories accordingly.
- GajShield Threat Lab
Proactive virus detection, Robust and inherent immune system that integrates Zero-Hour (Zero-Day) Virus Outbreak Protection to shield enterprises in the earliest moments of malware outbreaks, and right through as new variants emerge. By proactively scanning the Internet and identifying massive virus outbreaks as soon as they emerge, proactive virus blocking is effective and signature independent. At the Threat Lab, a database of real-time spam outbreaks is collected and compiled and maintained, through consultation with global Internet Service Providers. Patterns are analyzed, categorized, and cross-matched using algorithms, run to optimize the detection of repeating patterns and their sources. This database, containing approximately over six million signatures, is continuously updated with more than 30,000 new unique signatures added hourly.
Gateway Anti-Malware
- Powerful and Real-Time protection from Virus outbreaks
- Scans HTTP, HTTPS, FTP, POP3, SMTP & SMTPS traffic
- Detects and removes viruses, worms and all kinds of malware
- Instant identification of virus-infected users
- ZERO Hour Virus protection
- Spyware, Malware, Phishing protection
- Automatic real-time Virus update
- Complete protection of traffic over all protocols
- Last virus update definition
- Complete report
Security-Driven Networking
GajShield enables best-of-breed software-driven networking that is both high-performance and protected. GajShield Data Security Firewall featuring multi-core architecture to deliver faster network management with extreme security performance. GajShield has robust threat protection, including Layer 3 through Layer 7 security controls and data-level visibility. Featuring Complete threat protection, including firewall, antivirus, intrusion prevention system (IPS), and application control High-throughput SSL inspection with minimal performance degradation, ensuring that organizations do not sacrifice throughput for complete threat protection against zero-day threat. Web filtering to enforce internet security and Highly scalable & throughput overlay VPN tunnels to ensure that confidential traffic is always encrypted.
Virtual Private Network
An Effective Security and Remote Access Solution For Your Business Need
Businesses today have various work locations and access information and data, various employees and stakeholder while accessing these data open a threat vector for hackers to enter network using such an opportunity, thus, maintaining a secured connectivity while connecting with the organization’s network is essential to protect from a data breach attempt.
The Data Security Firewall creates virtual private network (VPN) which is a network that is completely isolated from the rest of the Internet. VPN provides a functionality to people, businesses, military and governmental organizations to remotely use network resources in a secured manner. Virtual private networks use site-to-site as well as remote access methods to function and are free to use for the most part. VPNs consist of an array of encryption services that allow a secured connection to be formed. A virtual private network (VPN) extends a private network across a public network and enables the users to send and receive the data across shared or public networks as if their computing devices were directly connected to the private network. As a result of this, Applications running across VPN benefit hugely from the functionality, security and management of the private network.
VPNs are extremely beneficial to organizations that are especially situated across multiple geographical locations. VPNs also allow employees to securely access a corporate intranet while they are located outside the office. This feature could be extremely beneficial to Road-warriors who are always moving. Additionally, VPNs are used to securely connect geographically separated offices of an organization, to create one cohesive network.
A VPN is created by establishing a virtual point-to-point connection through the use of dedicated connections, traffic encryption or virtual tunneling protocols. If we consider a user’s perspective, the resources available within the private network can be accessed remotely. VPN facilitates privacy because the user's initial IP address is replaced with the one from the VPN provider. This process allows the subscribers to attain an IP address from any gateway city that the VPN service provides. For instance, you may be situated in San Francisco, but with a VPN, you can appear to live in Mumbai, New York, or anywhere.

VPN Network Image
- Client to site
- Site to site
- Site to data centers
- Site to cloud
Highlight Icons
- Save from Man in the middle attacks
- Strong Encryption
- High speed secured data transfer
- Multiple endpoint
- SSL and IPsec VPN tunnels
Security with VPN
Security is the main reason why corporations have preferred the use of VPNs for years. There are increasingly simple methods to intercept data traveling to a network. VPNs use advanced encryption protocols and secure tunneling techniques to encapsulate all online data transfers. Most savvy computer users wouldn't dream of connecting to the Internet without a firewall and up-to-date antivirus. Evolving security threats and ever-increasing reliance on the Internet makes VPN an essential part of well-rounded security
VPN Protocols
PPTP - The main selling point of PPTP is that it can be simple to setup. PPTP tunnels form a point-to-point connection over the GRE protocol. Unfortunately, the security of the PPTP protocol has been called into question in recent years. It is strong, but not the most secure.
L2TP/IPsec - L2TP over IPsec is more secure than PPTP and offers more security features. L2TP/IPsec is a way of implementing two protocols together in order to gain the best features of each. In this case, the L2TP protocol is used to create a tunnel and IPsec provides a secure channel. This makes for an impressively secure package. It is a client to site VPN.
Ipsec: IPSec is a site to site VPN and IPSec suite enables advance VPN features. IPSec acts at the network layer, protecting and authenticating IP packets between a Firewall and other participating IPSec devices (peers), such as other Firewalls, routers, the Secure VPN Client and other IPSec-compliant products.
VPN WITH GAJSHIELD
GajShield provides Industry Standard IPSec (Site-Site), L2TP and PPTP VPN (Client-Site/Remote Access) along with High Availability for IPSec. GajShield incorporates Strong Authentication with RSA SecureID, VASCO tokens, Radius, LDAP and Active Directory (along with 2FA) to avoid any kind of interception in the network and the communication with the help of UserSense. Besides this, a lot of emphasize is given on the Encryption of the data and Authentication of the users aiming to access or transfer the data. GajShield uses DES, 3DES, AES encryption and Hash Algorithms like MD5, SHA1 and SHA2 for encryption purposes and Pre-shared key and Digital Certificates for secured Authentication. GajShield also supports Internet Key Exchange that is, IKEv1 or IKEv2, (depending on the version) which is the protocol used to setup a security association (SA) in IPSec protocol suite
GajShield aims to further secure the network by providing additional features in VPN like IPSec NAT traversal, Dead Peer detection and PFS support.
IPSec VPN tunnel up/down logs and Active VPN user logs are provided to monitor the details such as IP Address, Status of the VPN and the type of VPN by the users who are connected to the VPN.
Features
- VPN Supported: IPSec, L2TP, PPTP, SSL VPN
- Encryption - 3DES, DES, AES 128, AES 192, AES 256
- Hash Algorithms - MD5, SHA-1, SHA-2
- Authentication – Pre-shared key, Digital certificates (X.509), Xauth
- Supports PKCS#7, PKCS#10 & PKCS#12 Standards
- Supports IKEv1, IKEv2 with EAP
- VPN Protocols supported - ESP & GRE
- IPSec NAT Traversal
- Site-Site, Client-Site support
- VPN Client pass through
- Dead peer detection and PFS support
- VPN Acceleration
- Diffie Hellman Groups - 1,2,5,14,15,16
- External Certificate Authority support
- Local Certificate Authority support like create/renew/delete self signed certificate
- Export Road Warrior connection configuration
- Domain name support for tunnel end points
- Hardware Token: RSA, Vasco
- VPN connection failover
- Bandwidth Management of VPN traffic
- In-depth reporting with real time VPN link status
- UserSense authentication support for VPN traffic
Page 1 of 17
