Contextual Intelligence Engine
Contextual Intelligence Engine is a technology that allows to gain advanced visibility of data transaction over applications that uses network. Context based security approach is a step ahead from traditional firewall capabilities. Using deep inspection at Different Levels for advanced security, Contextual Intelligence Engine understands the application and its data context. It allows to create context of SaaS applications and understand its usage, much deeper than just the application. Combined with Machine Learning, contextual intelligent engine helps in finding anomalies.
While traditional security systems’ primary focus is to prevent the wrong people from accessing critical information, context-based security’s focus is to enable the right people to access the right type and the right amount of information in the right situations.
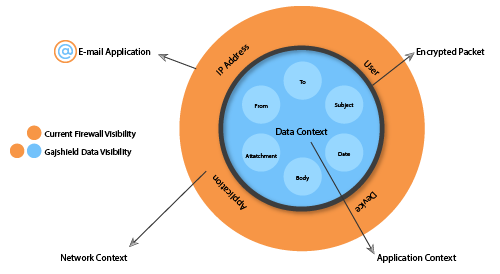
- Who is Using (IP/User ID)?
- When (Data & Time Details)
- How (The nature/Intention of application use)
- From (Remote or Physical Presence)
- To (The recipient of the communication)
- Sender (Email ID)
- Recipient (To, CC, BCC)
- Data (Subject, Mail Body, Signature and Attachments)
- Content of File (Deep Inspection of File Content)
- Other Details (Hash value, Fingerprint, Meta Info & Watermark).
Contextual Intelligence for Security?
There is Increase in adaptation of Cloud/SaaS applications by business for allowing the ease of access to employees to certain data and services. These Businesses need context-intelligent security systems to ensure they secure all their business-critical data without compromising on the convenience of accessing data in exigent situations. This gives the business a robust layer of security that is also flexible and intelligent enough to allow access under the right set of circumstances. This expedites business processes and enhances business performance since sharing and accessing the necessary data is facilitated. Simultaneously, the system also maintains the confidentiality of business data by monitoring for abnormal network activity and preventing unauthorized access based on contextual information.
Features
- Increased Visibility on data passing through SaaS applications.
- Advanced Network Visibility
- Limit the use of applications to business use only.
- Better security for Mobile workforce.
- Seamless security for roaming users by.
- Better Gateway Security
- Uncompromised End Point Performance

Complete Visibility
The most compelling reason as to why data visibility is a must for data security is simply that it is impossible to protect what you can’t see. An enterprise data must be monitored everytime it exists the organization. That means having real-time knowledge of:
- Every piece of information that is transmitted to, from, and within the organizational network.
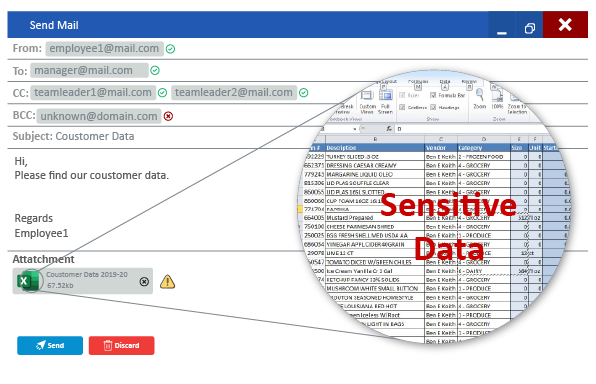
- The source and destination (E.g. URLs, email IDs, body content, subject, attachments, content of attachments etc.) of every inbound and outbound communication.
- Gains visibility on internet activities of computer devices used by the enterprise, which includes all the laptop computer devices used by employees from other remote locations.
At GajShield we understand how enterprises workforce make use of data in their day to day activities and the importance of data for business continuity. These data are very useful and if fallen in wrong hands, can result into disastrous situations. To protect these data and prevent data exploitation, one must have visibility beyond just the traditional Layer 7 to understand i.e. understand of further contextual data that is associated with the identified application in use.
At GajShield we understand how enterprises workforce make use of data in their day to day activities and the importance of data for business continuity. These data are very useful and if fallen in wrong hands, can result into disastrous situations. To protect these data and prevent data exploitation, one must have visibility beyond just the traditional Layer 7 to understand i.e. understand of further contextual data that is associated with the identified application in use.

Using GajOS Bulwark, GajShield Data Security Firewall provides
- Complete visibility of the applications and bandwidth used.
- Complete visibility of evasive applications like P2P and Skype application.
- Complete insight on :
- Content upload via Web uploads ex: webmail, Social networking sites, Blogs, Instant Messaging, Mail.
- Content sent through email.
- Content sent through Instant Messaging.
- Comprehensive reporting on :
- Top Internet Users.
- Top Bandwidth Users.
- User/Group Activity.
- Application Traffic.
- P2P Usage.
- URL/Category Usage.
- Total Internet Traffic.
- Application Traffic, Total Traffic, Application set and application detail.
- Web Browsing by URL, Category and User.
- Trend Analysis of applications, users and bandwidth.
- Current, Daily, Monthly, Yearly reports And much more.
