Virtual Private Network (VPN): The “encrypted tunnel” that protects your data from breaches
The fear of being watched and your data being illegally accessed by malicious entities somewhat spoils the experience of using the internet. As you know, entering the world wide web leaves users vulnerable to nasty cyber threats such as phishing, ransomware and DDoS attacks that can lead to losses in terms of money and data. Therefore, users tend to be more cautious while opening downloads from any source or while visiting websites that may contain multiple pop ups. Most of all, sharing sensitive data across unencrypted channels can be nerve wracking for internet users. A Virtual Private Network (VPN) provides a metaphorical data security blanket for the safe transmission of sensitive information from one end of the internet spectrum to another..
How does a VPN work?
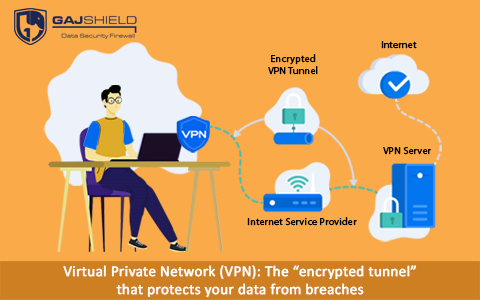
The data that goes through a VPN is encrypted. In other words, one can say that this creates a kind of tunnel for your sensitive data to pass without being identified by external entities. The scrambled, undecipherable data will be incomprehensible to such entities, making it doubly secure. A dedicated VPN service provider can create such a blanket network and encrypted connections between different devices and applications involved in them.
The encryption and decryption of data transmitted between one device and another are carried out through specialised encryption keys that are set up for each device connected to the network. This ensures that the data transfer channels remain secure and private even when a public Wi-Fi network is being used for data transmission. So, even if a cybercriminal infiltrates the Internet Exchange Point (IXP) through which all the user data passes, they wouldn’t be able to access or understand the data and use it illegally.
VPNs utilise the principle of isolation to optimise access control for users. So, unless a device is connected to the VPN network, it cannot access the data that passes through it. Businesses use VPNs to regulate which users would be able to access which digital resources. Essentially, businesses set up multiple VPNs, with each network linked to different types of company resources. Such an arrangement allows them to have multiple levels of encryption for their employees. In this way, VPNs are vital data security resources to prevent insider attacks and social engineering, two of the more common cyber threats in today’s day and age.
Basically, VPN not only creates a tunnelling effect for your data but also encrypts data so that it is incomprehensible and inaccessible to unauthorised entities while it is being shared with other authorised users (who are also a part of the same VPN).
One of the biggest advantages of using a VPN is that it makes users immune to price discrimination. As you may know, certain e-commerce businesses charge exorbitant prices for a given product to users from certain countries to unethically beef up their profits. A VPN makes it impossible for businesses to track down the location of users, thereby preventing their dynamic pricing algorithms from kicking into gear and displaying the beefed prices for their goods to users from any region.
What are the problematic aspects of VPNs?
VPNs are not without their fair share of flaws. Despite the data security such virtual networks provide, VPN users may face network problems due to the following inherent VPN issues:
VPN slows down your network
A VPN elongates the path through which your data flows by rerouting your network and encrypting data. This causes your internet speed to reduce to an extent. Sharing large files over a VPN may, as a result, become cumbersome for users. Additionally, streaming content over a VPN is also slow as compared to a regular network. This problem can be rectified to an extent by paying for premium VPN services offered by the likes of NordVPN and ExpressVPN. Data transfer through such premium networks is still slow compared to regular ones, but quicker compared to other VPNs.
VPN encryption quality cannot be checked
Perhaps the biggest issue connected with VPNs, this issue makes it impossible for users to verify whether a VPN does what their service provider promises. Also, since several users may not have adequate knowledge regarding data encryption, they cannot verify the quality of the same in a given VPN. These problems become doubly damaging for users as they only understand the weaknesses in their VPN when something goes wrong.
VPNs are blocked by certain services and governments
Certain services or websites, such as HULU, YouTube, and Netflix, block IP addresses that access their website from a massive number of network connections—a trait found in VPN users who commonly share a common server with a single IP address. In addition to such services, VPNs are also banned by certain governments. Such services and countries are opposed to the concepts of user anonymity that VPN brings as they view it as a potential data security threat.
Despite these limitations, using a VPN is hugely beneficial for individuals and businesses, especially ones that collect and use sensitive customer data.
Gajshield’s data security firewall creates a VPN that can safeguard your data and keep it away from cybercriminals and vicious cyber-attacks. Apart from this, our firewall systems and other data security applications and tools can be used to create a formidable cybersecurity blanket for your critical business operations that makes them impervious to all kinds of network threats.
Kindly contact us to discover our complete suite of data security products and services.
Get In Touch With Us
Subscribe to our Newsletter
2025 © GajShield Infotech (I) Pvt. Ltd. All rights reserved.
