Complete Visibility
Gain Deep Dive into Data Context of Application
It has been evident and have become a thumb rule for cybersecurity to have visibility on things we want to protect. Simply, you cannot protect that you cannot see. While Cybersecurity is never a static, one-time initiative but an ongoing process that should always be top-of-mind for CSOs, CIOs, and other IT leaders. To that end, technology and security leaders should always have access to information regarding the security of their enterprise networks possible only if they have visibility not only on their network but beyond just the network. In fact, not just the leaders but even employees need real-time Data visibility to report any damage to or illicit use of the organization’s Critical Data. And ensuring enterprise-wide Data visibility should be a priority even if the organization uses the most cutting-edge cybersecurity tools and technologies. That’s because cybersecurity systems, while generally being effective at keeping bad actors out and sensitive data in, cannot keep your Data protected all the time and from all threats if it does not have visibility. There can always emerge newer forms of threats that may require the immediate attention of an enterprise’s cybersecurity personnel and leaders. And the time it takes between a threat’s incipience and the cybersecurity team’s awareness of it can be the difference between security and enterprise-wide mayhem.
The most compelling reason as to why data visibility is a must for data security is simply that it is impossible to protect what you can’t see. An enterprise data must be monitored everytime it exists the organization. That means having real-time knowledge of:
- Every piece of information that is transmitted to, from, and within the organizational network.
- The source and destination (E.g. URLs, email IDs, body content, subject, attachments, content of attachments etc.) of every inbound and outbound communication.
- Gains visibility on internet activities of computer devices used by the enterprise, which includes all the laptop computer devices used by employees from other remote locations.
At GajShield we understand how enterprises workforce make use of data in their day to day activities and the importance of data for business continuity. These data are very useful and if fallen in wrong hands, can result into disastrous situations. To protect these data and prevent data exploitation, one must have visibility beyond just the traditional Layer 7 to understand i.e. understand of further contextual data that is associated with the identified application in use.
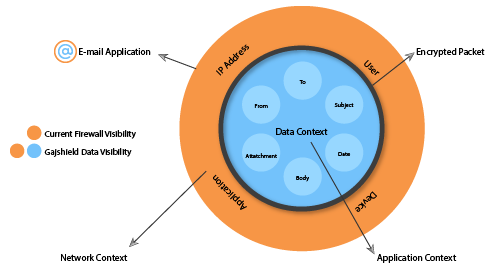
GajShield Data Security Firewall uses Contextual Intelligence Engine and Combines it with advanced reporting capabilities of GajOS: Bulwark for Enterprises to augment their traditional layer 3 (network level) security with a layer 7 (application level) security solutions and deep dive past than just the layer 7 into Data Context to create contextual information. GajShield Data Security Firewalls perform Data Layer inspection with the help of Contextual Intelligence Engine to create data context and analyze a broader range of parameters with greater in-depth data layer visibility, extending the visibility to more data like Email ID, Sender ID, recipient ID, CC mentions, Subject, Mail Body, Signature, File Content, downloader, uploader etc. across web traffic and SaaS applications to identify abnormal behaviors that may indicate potential cyber and data threats.
Analyzing these parameters, the Data Security Firewall determines the safety and legitimacy of communications & transactions and takes necessary actions to prevent data exploitation and this capability can is useful in mitigating the impact of a zero-day attacks.
Using GajOS Bulwark, GajShield Data Security Firewall provides
- Complete visibility of the applications and bandwidth used.
- Complete visibility of evasive applications like P2P and Skype application.
- Complete insight on :
- Content upload via Web uploads ex: webmail, Social networking sites, Blogs, Instant Messaging, Mail.
- Content sent through email.
- Content sent through Instant Messaging.
- Comprehensive reporting on :
- Top Internet Users.
- Top Bandwidth Users.
- User/Group Activity.
- Application Traffic.
- P2P Usage.
- URL/Category Usage.
- Total Internet Traffic.
- Application Traffic, Total Traffic, Application set and application detail.
- Web Browsing by URL, Category and User.
- Trend Analysis of applications, users and bandwidth.
- Current, Daily, Monthly, Yearly reports And much more.
